Subdomailing: The Campaign That Abused Thousands of Hijacked Subdomains

Back in my Guard.io days, Nati Tal and I wrote about one of the most impressive subdomain takeover campaigns we’d ever seen—a sprawling, industrial-scale operation that weaponized thousands of abandoned subdomains belonging to major brands. This wasn’t your everyday security blog; this was Subdomailing—a term I coined to describe the full-blown subdomain hijack factory that flooded the internet with millions of spam emails.
Subdomain Takeovers 101: How Does This Work?
Subdomain takeovers happen when a subdomain is configured to point to an external resource that is no longer in use or has been abandoned. This creates a perfect loophole that attackers can exploit in two main ways:
- Dangling CNAME / NS Records (Service Takeover) – A subdomain is pointing to a third-party service (e.g., Shopify, AWS S3, Heroku, etc.), but the associated resource has been deleted or is no longer owned by the company. If the DNS record remains active, an attacker can claim the abandoned service and take over the subdomain.
- Expired Domain Takeover (Domain-Level Takeover) – A subdomain (
sub.example.com) is configured to point to a domain (expired-domain.com) that has expired or was not renewed. If an attacker registers the expired domain, they automatically control all subdomains pointing to it—often without touching any DNS settings.
In both cases, the hijacked subdomain retains its original branding and trust, allowing attackers to:
✅ Host phishing pages that seem completely legitimate.
✅ Execute JavaScript within the target domain’s context, potentially granting access to sensitive data, such as cookies.
✅ Send millions of spam emails from what appears to be a high-reputation domain which bypasses all spam filters.
SPF Takeovers: Hijacking Email Without Even Taking a Subdomain
Subdomain takeovers weren’t the only trick up the attackers’ sleeves. Another major attack vector in this campaign was SPF record takeovers, a sneaky way to hijack email-sending permissions without needing full control over a domain.
🕵️ How SPF Takeovers Work
SPF (Sender Policy Framework) records define which mail servers are allowed to send emails on behalf of a domain. But a misconfigured SPF record can introduce vulnerabilities:
- SPF Includes an Abandoned Domain – If an SPF record includes an external domain that expires or is abandoned, an attacker can register that domain and suddenly gain permission to send emails on behalf of the original domain.
- Overly Permissive SPF Records – Some organizations use
+allor allow*.subdomain.com, making it trivial for attackers to send emails that pass SPF checks. - Typos in SPF Records – A simple typo (
spf.g00gle.cominstead ofspf.google.com) can allow an attacker to buy the typo domain and hijack SPF records for email spoofing.
Once an attacker hijacks an SPF record, they can send fully authenticated emails on behalf of a major brand, making phishing and spam much harder to detect.
The Campaign That Weaponized Takeovers
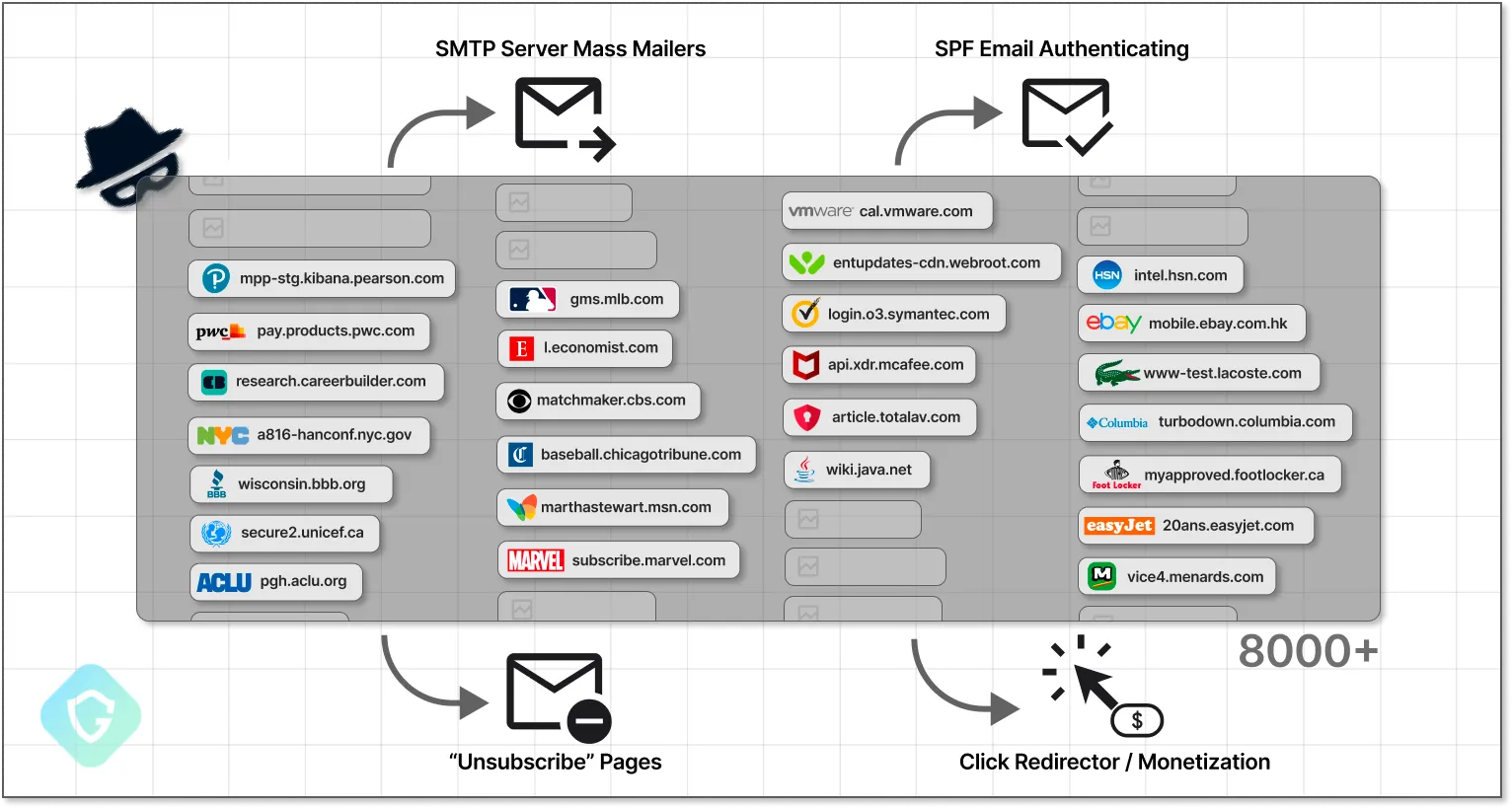
We uncovered a massive, automated campaign that exploited thousands of abandoned subdomains from Fortune 500 companies, universities, and government agencies. This wasn’t just a handful of isolated cases—this was industrial-scale abuse, with attackers systematically scanning for vulnerable subdomains and taking them over to distribute millions of spam emails.
Imagine getting an email from support.yourbank.com, only to realize later it was a scam. The kicker? The attackers didn’t need to hack anything—they just claimed an abandoned subdomain and used it for their own spam operation.
When Cyber Companies Jumped on the Term
Not long after we exposed this, cybersecurity companies started using "Subdomailing" as part of their marketing for their products. The most notable example? RedSift, which even launched a tool named Subdomailing to help organizations scan for vulnerable subdomains. The term spread quickly in the security space, reinforcing the importance of DNS hygiene and attack surface management.

The Lesson? Clean Up Your DNS!
This whole saga was a brutal wake-up call for companies to:
🔍 Clean up abandoned subdomains before someone else claims them
🛑 Monitor expiring domains and reclaim them before attackers do
📧 Harden SPF records to prevent unauthorized email senders
⚠ Avoid typos & overly permissive SPF configurations
Subdomain takeovers and SPF misconfigurations aren’t just an edge-case vulnerability—they’re a goldmine for attackers, and organizations need to treat them as a real and ongoing security threat.
👉 Want the full breakdown? Check out the blog here.

